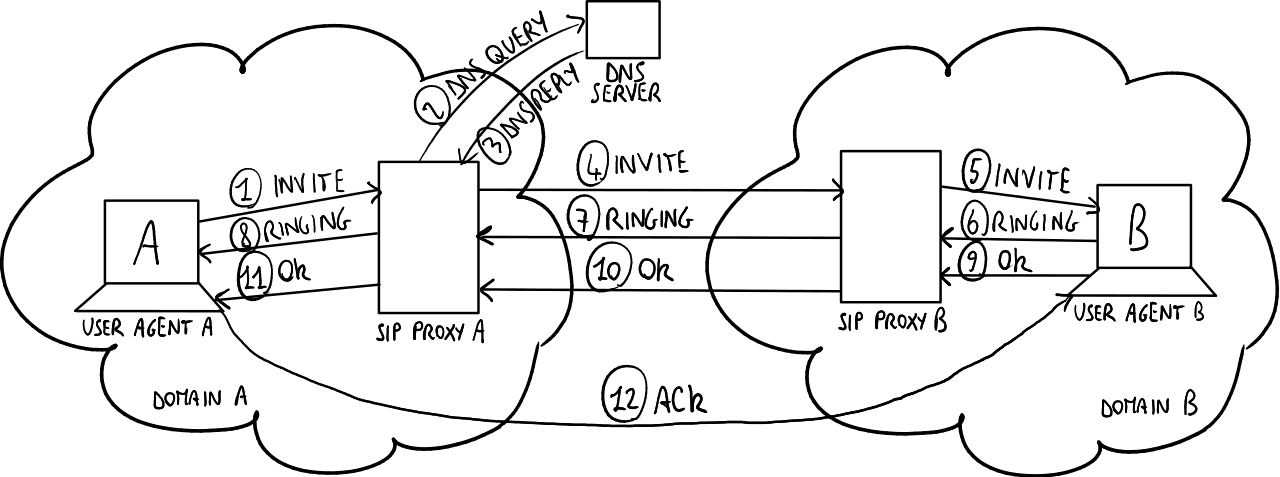
SIP attack- MLPP DoS
Today we can easily say that SIP is the leading protocol on the VoIP systems. The success of SIP is certainly result of simple and robust architecture of this protocol. However, like every other protocol SIP has several weaknesses.